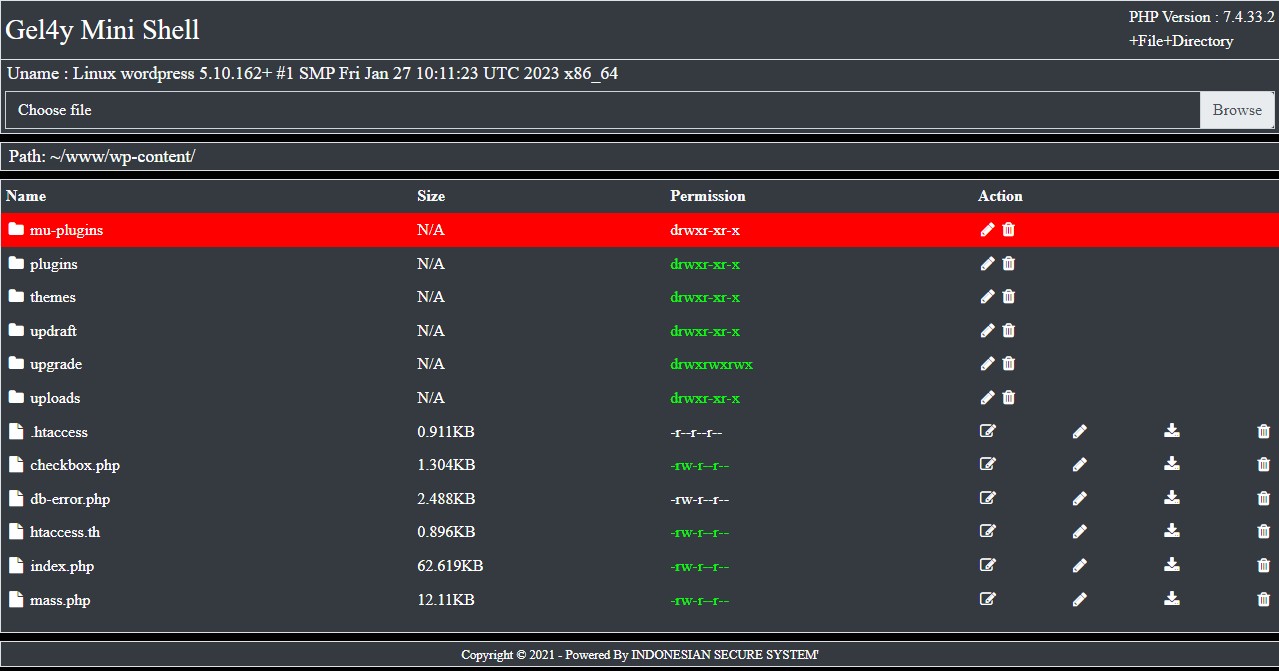
GEL4Y Tiny Shell size of very very small.
Title: Bypassing Linux Systems with PHP Shell: Techniques and Mitigation
Introduction:
In the realm of Linux systems, both security researchers and malicious actors often leverage PHP-based shells to gain unauthorized access to target systems. However, system administrators and security professionals can take various measures to prevent and detect such attacks. This article delves into the techniques used to bypass Linux systems using PHP shells and discusses the countermeasures that can be employed to mitigate these threats effectively.
- Exploiting Security Vulnerabilities: Many PHP-based shell scripts operate by exploiting security vulnerabilities present in the target system. For instance, leveraging vulnerabilities in web servers like Apache or Nginx can grant access to the system. Therefore, it’s crucial for system administrators to regularly check for security updates for web servers and other software components.
- Leveraging Unloaded PHP Modules: Some PHP-based shell scripts may function by utilizing PHP modules that are not installed on the target system. Functions like
system()orexec()might be disabled on the target system, preventing attackers from executing the shell script. System administrators can mitigate such attacks by disabling unnecessary PHP modules. - File Management Exploits: Certain PHP-based shell scripts gain access to the target system through file management exploits. For example, by exploiting upload directories or backup files, attackers can inject malicious code into the system. System administrators can prevent such attacks by regulating access permissions on sensitive files and directories and implementing protective measures such as firewalls and security software.
- Firewall and Monitoring Solutions: System administrators can monitor PHP shell activities on target systems using solutions like firewalls, network monitoring, and Security Information and Event Management (SIEM) tools. These solutions help in detecting abnormal network traffic and file activities, aiding in the identification of attacks.
- Strong Passwords and Authentication Methods: By implementing robust password policies and employing authentication methods like two-factor authentication, system administrators can restrict unauthorized access to target systems. These measures help mitigate PHP shell attacks by thwarting unauthorized access attempts.
Conclusion:
PHP shell bypass attacks pose a significant security threat to Linux systems. However, with appropriate security measures and monitoring solutions in place, these attacks can be detected and mitigated effectively. Consistently monitoring security updates, disabling unnecessary PHP modules, and implementing strong authentication mechanisms are critical steps to enhance the security of target systems and mitigate the effectiveness of PHP shell bypass attacks.