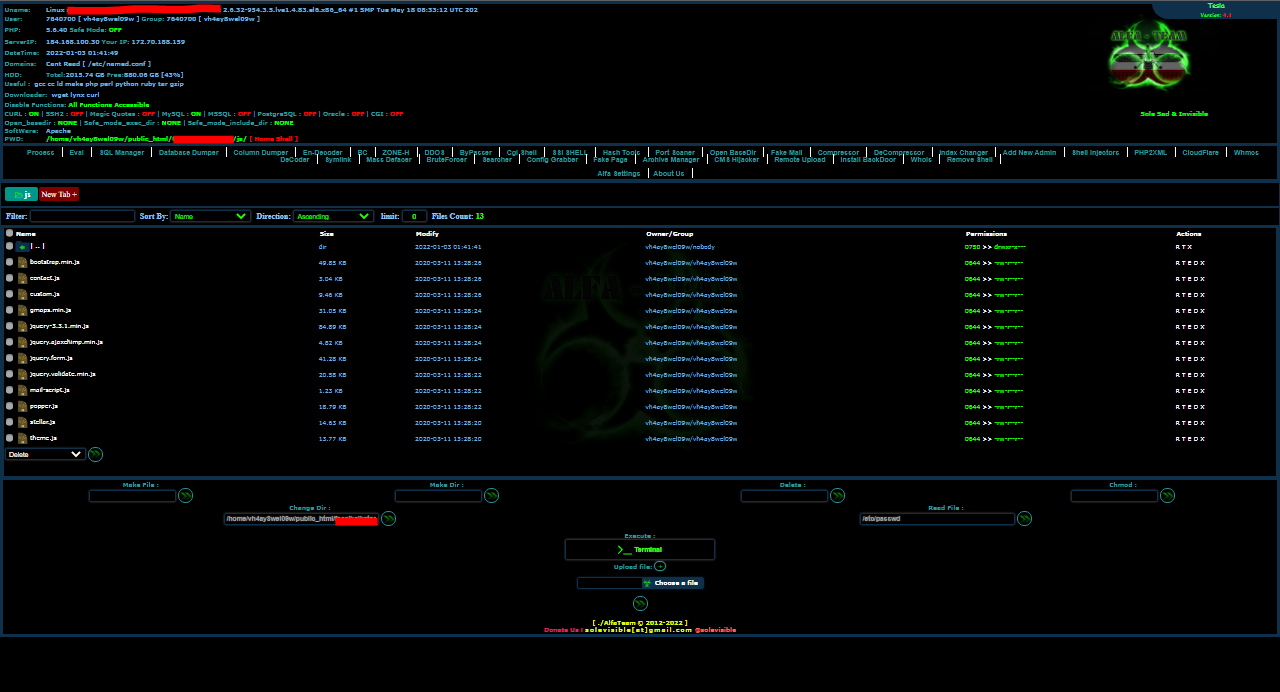
Alfa Shell is a web building shell tool. Therefore, you need to use a web browser to open Alfa Shell. You can open Alfa Shell by following the steps I will tell you:
1-Open your web browser (you can use any browser such as Google Chrome, Mozilla Firefox, Microsoft Edge).
2-Go to Alfa Shell’s official website or get the address of a server hosting Alfa Shell.
3-If you go to the official website of Alfa Shell, you will usually encounter a path where you need to log in. Enter login information such as username and password. If you received the address of a server hosting Alfa Shell, type the address of the server to your browser’s address and press Enter.
4-If you entered the login information correctly or accessed the server correctly, the Alfa Shell interface will open. This narrative usually includes a command line-like area. You can run your commands in this area.
good forums.
Exploring the Features and Usage of PHP Alfa Shell
In the ever-evolving landscape of cybersecurity threats, web shells have become a notorious tool for attackers seeking unauthorized access to web servers. Among these, PHP Alfa Shell stands out as a potent and feature-rich web shell that poses significant risks to web server security. In this comprehensive article, we’ll delve into the functionalities, features, and usage of PHP Alfa Shell.
Understanding PHP Alfa Shell:
PHP Alfa Shell is a sophisticated web shell written in PHP, designed to provide attackers with remote access and control over compromised web servers. It offers a wide range of features and capabilities, making it a popular choice among cybercriminals for carrying out various malicious activities.
Key Features of PHP Alfa Shell:
- Remote Command Execution: One of the primary features of PHP Alfa Shell is its ability to execute commands directly on the compromised server. Attackers can leverage this feature to perform tasks such as file manipulation, data exfiltration, and privilege escalation.
- File Management: PHP Alfa Shell allows attackers to upload, download, edit, and delete files on the target server, providing them with full control over its file system. This capability is often exploited for purposes such as planting backdoors, modifying website content, or stealing sensitive data.
- Backdoor Access: Once deployed on a web server, PHP Alfa Shell acts as a backdoor, enabling persistent access for attackers even if initial points of entry are discovered and patched. This backdoor access facilitates long-term control over compromised servers, allowing attackers to maintain their presence undetected.
- Security Evasion: PHP Alfa Shell employs various techniques to evade detection by security measures. These may include obfuscation, encryption, or polymorphic code generation, making it challenging for defenders to identify and mitigate its presence on compromised servers.
- Exploit Automation: PHP Alfa Shell may include features for automated exploitation of vulnerabilities in web applications and server software. Attackers can use these capabilities to rapidly compromise multiple systems, increasing the scale and impact of their attacks.
Usage of PHP Alfa Shell:
The usage of PHP Alfa Shell typically involves the following steps:
- Initial Compromise: Attackers gain initial access to the target server through vulnerabilities in web applications, misconfigurations, or social engineering attacks.
- Deployment: Once access is gained, attackers upload PHP Alfa Shell to the compromised server, typically through file upload vulnerabilities or insecure file transfer protocols.
- Execution: Attackers access PHP Alfa Shell through a web browser or HTTP client, providing them with a web-based interface for executing commands and managing the compromised server.
- Malicious Activities: With PHP Alfa Shell deployed, attackers can carry out various malicious activities, including data theft, website defacement, DDoS attacks, and propagation to other systems.
Mitigation Strategies:
To mitigate the risks associated with PHP Alfa Shell and similar web shells, organizations can implement the following strategies:
- Regular security audits to detect and remove unauthorized files or scripts, including web shells.
- Enforce strict access control measures to prevent unauthorized upload and execution of PHP files on the server.
- Deploy web application firewalls (WAF) capable of detecting and blocking malicious HTTP requests associated with web shells.
- Keep server software and web applications up-to-date with the latest security patches to prevent exploitation of known vulnerabilities.
Conclusion:
PHP Alfa Shell represents a significant threat to web server security, enabling attackers to compromise and manipulate sensitive data with ease. Its sophisticated features and capabilities make it a formidable tool in the hands of cybercriminals. By understanding its functionalities, features, and usage, organizations can better defend against the risks posed by PHP Alfa Shell and safeguard their web assets from exploitation.