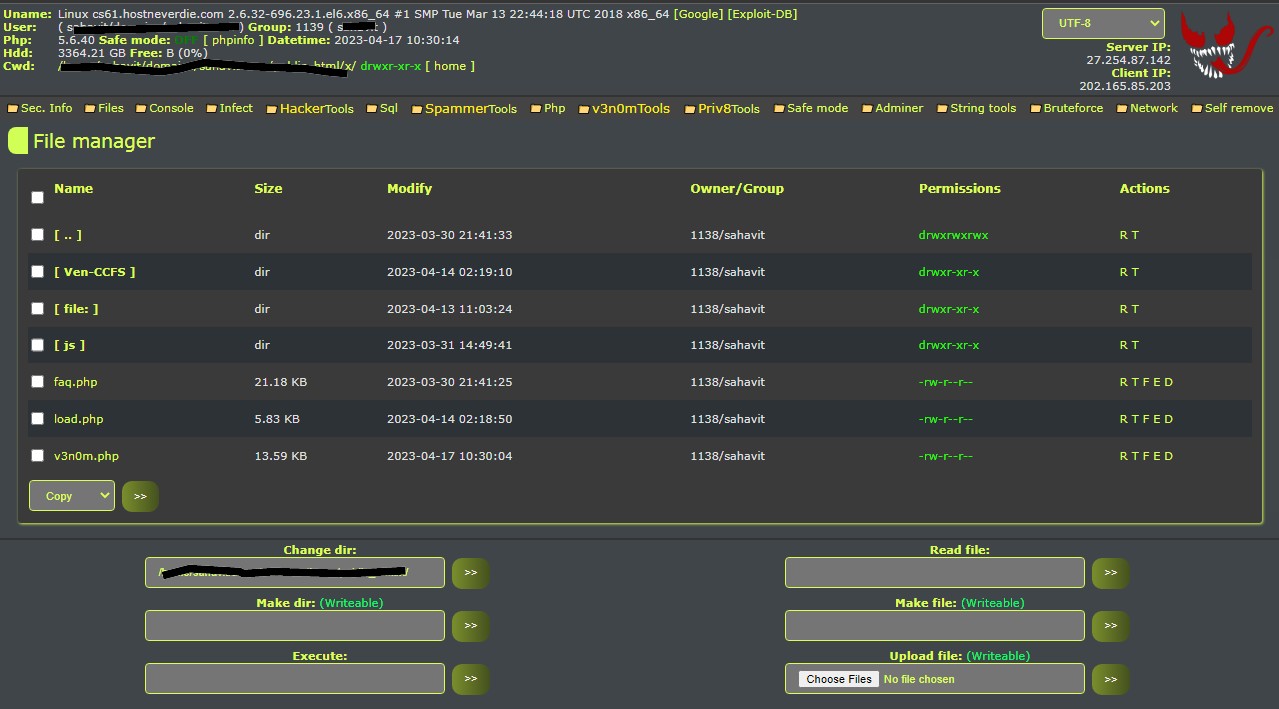
Introduction to v3n0m WSO PHP Shell
v3n0m WSO PHP Shell is a powerful web shell commonly used by attackers to gain unauthorized access and control over web servers. This PHP shell is part of the WSO (Web Shell by Orb) family and is known for its robust feature set and stealthy operation.
Features:
- Remote Command Execution: v3n0m WSO PHP Shell allows attackers to execute commands directly on the compromised server, enabling various malicious activities such as file manipulation, data exfiltration, and privilege escalation.
- File Management: With v3n0m WSO PHP Shell, attackers can upload, download, edit, and delete files on the target server, giving them full control over its contents.
- Backdoor Access: Once deployed on a web server, the shell acts as a backdoor, providing persistent access for attackers even if initial points of entry are discovered and patched.
- Security Evasion: v3n0m WSO PHP Shell is designed to evade detection by security software, making it challenging to identify and remove from compromised servers.
Use Cases:
v3n0m WSO PHP Shell is utilized by malicious actors for various nefarious purposes, including:
- Data Theft: Attackers use the shell to steal sensitive data stored on the server, such as user credentials, financial information, and intellectual property.
- Website Defacement: The shell can be used to deface websites hosted on the compromised server by modifying their content or displaying unauthorized messages.
- Distributed Denial of Service (DDoS): Attackers may leverage the compromised server’s resources to launch DDoS attacks against other targets, disrupting their availability.
Mitigation Strategies:
To mitigate the risks associated with v3n0m WSO PHP Shell and similar threats, organizations can implement the following strategies:
- Regular Security Audits: Conduct regular security audits of web servers to detect and remove any unauthorized files or scripts, including web shells like v3n0m WSO.
- Access Control: Enforce strict access control measures to prevent unauthorized upload and execution of PHP files on the server.
- Web Application Firewalls (WAF): Deploy WAF solutions capable of detecting and blocking malicious HTTP requests associated with web shells.
Conclusion:
v3n0m WSO PHP Shell poses a significant threat to web server security, allowing attackers to compromise and manipulate sensitive data with ease. By implementing robust security measures and staying vigilant, organizations can protect their web assets from the risks posed by v3n0m WSO PHP Shell and similar web shells.