Login user-pass: admin
Understanding ZeroByte PHP Shell
In the realm of cybersecurity, the term “shell” holds a significant weight. It refers to a command-line interface that allows users to interact with the operating system directly. Shells come in various forms, and one of the most intriguing ones is the ZeroByte PHP shell.
What is ZeroByte PHP Shell?
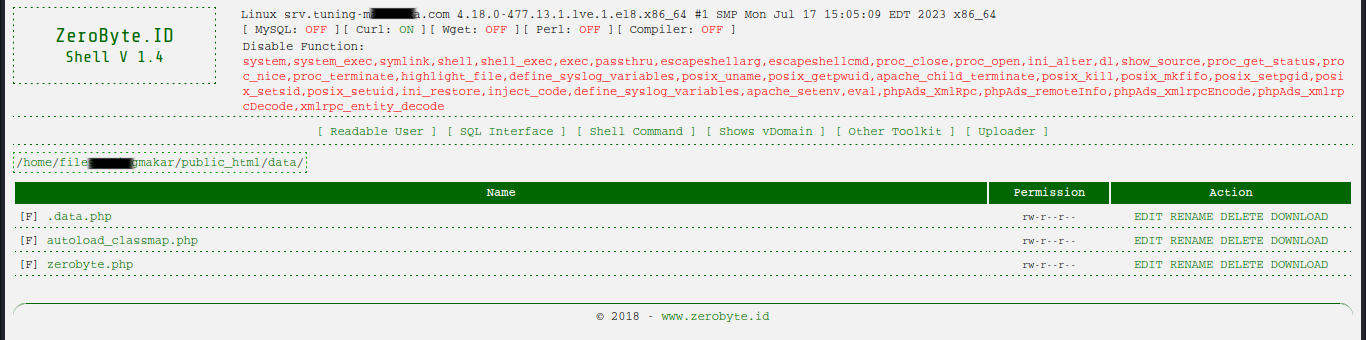
ZeroByte PHP Shell is a type of web shell, written in PHP programming language. It’s designed to be uploaded to a web server, granting the uploader remote access and control over the server through a web-based interface. The distinguishing feature of the ZeroByte PHP shell is its minuscule size – it occupies zero bytes on disk, hence the name.
Features and Functionality
Despite its small size, the ZeroByte PHP shell boasts a plethora of features typically found in larger, more complex shells. Some of its key functionalities include:
- Command Execution: Users can execute system commands directly from the web interface, enabling tasks such as file manipulation, process management, and data retrieval.
- File Management: The shell allows users to upload, download, edit, and delete files on the compromised server, facilitating data exfiltration or modification.
- Database Interaction: Users can interact with databases hosted on the server, executing SQL queries and managing database content.
- Security Evasion: ZeroByte PHP shell is designed to evade detection by security software. Its compact size makes it difficult to detect using traditional signature-based methods.
- Backdoor Access: Once uploaded to a server, the shell acts as a backdoor, providing persistent access for attackers even if the original point of entry is discovered and closed.
Use Cases
ZeroByte PHP shell is primarily utilized by malicious actors for unauthorized activities on compromised web servers. Some common use cases include:
- Data Theft: Attackers use the shell to steal sensitive data stored on the server, such as customer information, login credentials, or financial records.
- Distributed Denial of Service (DDoS): The shell can be used to launch DDoS attacks by leveraging the compromised server’s resources to flood target websites or servers with traffic, rendering them inaccessible.
- Website Defacement: Attackers may deface websites hosted on the compromised server by modifying their content or replacing it with malicious messages.
- Cryptocurrency Mining: The shell can be used to deploy cryptocurrency mining malware on the server, utilizing its computational resources to mine cryptocurrencies without the owner’s consent.
Mitigation Strategies
To protect against ZeroByte PHP shell and similar threats, organizations and website owners can implement the following mitigation strategies:
- Regular Security Audits: Conduct regular security audits of web servers to detect and remove any unauthorized files or scripts, including web shells.
- File Integrity Monitoring: Implement file integrity monitoring systems to detect unauthorized changes to server files and directories.
- Access Control: Enforce strict access control measures to limit the upload and execution of PHP files on the server.
- Web Application Firewalls (WAF): Deploy WAF solutions capable of detecting and blocking malicious HTTP requests, including those associated with web shells.
- Security Patching: Keep server software and web applications up-to-date with the latest security patches to prevent exploitation of known vulnerabilities.
Conclusion
ZeroByte PHP shell represents a potent tool in the arsenal of cybercriminals, enabling remote access and control of compromised web servers. Its small size and feature-rich functionality make it a challenging threat to detect and mitigate. By implementing robust security measures and staying vigilant, organizations can defend against the risks posed by web shells and safeguard their online assets.